Microcontroller-specific software to enable the hardware security features and abstract to the higher level basic software.
Benefits
Accelerated cryptographic calculations
Parallel execution of hardware-accelerated cryptographic calculations speeds up the entire process.
Hardware trust anchor
EB’s software in the trusted execution environment provides a secure key storage and monitors the host cores.
Maximum flexibility regarding hardware options
Abstractions of cryptographic calculations to the upper software layers ensure hardware independence.
Products:
EB zentur HSM Firmware
EB’s complete firmware software stack for a Hardware Security Module (HSM) implements security algorithms utilizing hardware acceleration mechanisms.
Features:
- Request dispatcher
- Key management
- Cryptographic hardware acceleration
- Cryptographic software algorithms
- Secure boot
- Secure storage
- Custom features
EB zentur Crypto Driver for hardware
The driver implements the interface into hardware acceleration modules HSM. It abstracts the cryptographic calculation to the upper software layers and allows seamless integration into EB tresos AutoCore.
Features:
- Implementation according to AUTOSAR 4.3
- Communication with HSM firmware
- Configurable with EB tresos Studio
- Flexible combination with EB tresos Crypto Driver Software
- Available for EB zentur HSM Firmware or alternative HSM implementations
EB zentur CryShe
Driver software for a secure hardware extension (SHE) module.
Features:
- Implementation to support AUTOSAR 4.x
- Utilize a SHE hardware module
- Support of HIS-defined APIs
- Configurable with EB tresos Studio
- Flexible combination with EB’s software libraries
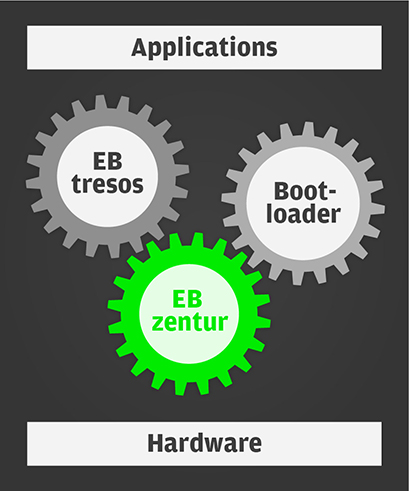
EB’s embedded security products
Components on the application layer
The security AUTOSAR basic software stack