
When teams set out to use Linux in safety-critical systems, the impulse is often to reach for certifications and checklists. Can we audit the kernel? What if we use static analysis? Can a consultant give us the green light? These are understandable questions, especially in industries where functional safety is mandatory. But they also reflect a deeper misconception.
Functional safety is not something that can be bolted on after the fact. It is not the result of a thorough paper trail or a successful audit. It is the outcome of decisions made at the architectural level, before a single line of code is evaluated for compliance. This blog explores why a successful safety story with open-source software begins with separation, control, and design, not documentation.
And it offers a look at how EB corbos Linux for Safety Applications turns this philosophy into practice.
The illusion of post-hoc certification
Many teams enter the safety discussion with the belief that if they just work hard enough, they can certify anything. This belief fuels a common but flawed strategy: start with standard Linux, then attempt to “safety-ify” it. Teams introduce audits, run formal tools, and generate long lists of artifacts. The result is a mountain of paperwork and very little progress.
The core issue is that Linux, by design, was never intended for functional safety. It is a vast, collaborative, community-driven OS optimized for general-purpose computing. It does not trace requirements. It does not prioritize determinism. And it changes rapidly, often without clear documentation or backward compatibility.
Trying to certify such a system retroactively often leads to a dead end. The effort grows exponentially, the arguments become increasingly strained, and the cost in both time and engineering hours skyrockets. More critically, safety assessors may ultimately reject the certification case, not because the system is unsafe, but because its safety cannot be convincingly demonstrated.
Functional safety is not just about behavior. It is about predictability, transparency, and trust. These are not qualities that emerge from audits alone. They must be designed in.

Why isolation and watchdogs matter more than paperwork
If the goal is to use Linux in a safety context, the right question is not how to certify Linux. It is how to keep Linux from interfering with what actually needs to be safe.
That insight shifts the challenge from certification to architecture. Functional safety is about defining a safety boundary and ensuring that nothing can violate it, especially a large complex OS like Linux.
This is where concepts like isolation, supervision, and failover become essential. Instead of trying to prove that Linux itself is safe, teams can design systems where Linux is prevented from causing harm. For example:
- Running Linux in a virtualized partition that is strictly separated from safety functions
- Using a watchdog supervisor to monitor the Linux domain and trigger recovery if it misbehaves
- Redirecting safety-critical I/O to dedicated hardware or microcontrollers
- Ensuring that any shared resources between Linux and safety functions are tightly controlled
These techniques are not new, but they are often overlooked in favor of audit-driven approaches. That is a mistake. Isolation gives you control. Watchdogs give you assurance. Together, they allow you to use powerful, flexible components like Linux without compromising safety goals.
It also shifts the burden of proof. You are no longer trying to argue that every line of Linux kernel code is safe. You are showing that the safety domain is protected from anything Linux might do, and that’s by design.

How EB corbos Linux flips the script on functional safety
EB corbos Linux for Safety Applications was created with this architectural mindset from the start. It does not try to make Linux safe. Instead, it makes Linux usable in safety systems, again, by design.
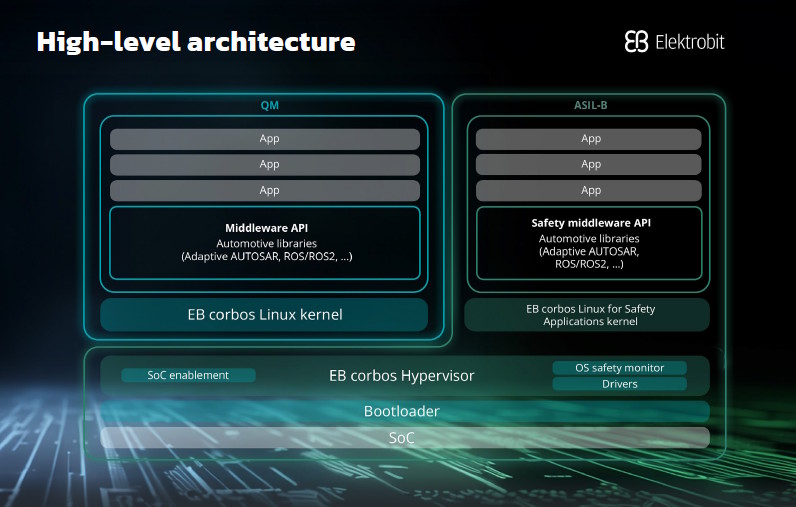
The key innovation is architectural separation. EB corbos Linux runs in a virtualized environment alongside safety-certified components. It is carefully constrained so that it cannot violate the safety boundary. The result is a system that supports rich, modern software stacks while maintaining the isolation and predictability required for safety arguments.
This architecture includes:
- A hardened Linux kernel configured specifically for real-time and embedded use
- A minimal, traceable safety supervisor that monitors Linux behavior
- Clearly defined inter-process communication mechanisms with controlled interfaces
- Support for ASIL decomposition, so that safety functions and non-safety functions can coexist with verifiable independence
In this model, Linux does not need to be certified. Instead, the safety case rests on the containment and supervision mechanisms. This not only reduces complexity, it dramatically improves the credibility and auditability of the overall system.
The real genius is in what this enables. EB corbos Linux gives developers the freedom to use modern tooling, middleware, and applications, without putting safety goals at risk. It brings the best of both worlds: open innovation and certified assurance.
Lessons for teams evaluating OSS for safety projects
The rise of open-source software in embedded systems is undeniable. Developers want to use what they know. Companies want to avoid vendor lock-in. And the capabilities of platforms like Linux are too valuable to ignore.
But safety demands discipline. Teams considering OSS for safety-critical applications should take away a few key lessons:
- Start with architecture, not compliance. Define your safety boundary. Design around containment. Choose components accordingly.
- Don’t try to certify what you can isolate. Use virtualization, inter-process separation, and watchdogs to keep untrusted code from impacting safety.
- Look for partners with real safety experience. Off-the-shelf OSS is powerful but uncurated. Solutions like EB corbos Linux bring structure, governance, and assurance into the mix.
- Understand your safety standards. ISO 26262, IEC 61508, and others do not require everything to be certified. They require a credible argument that risks are mitigated by design.
- Invest in the right tools and processes. Formal methods, traceability, and testing still matter. But they are far more effective when used in a system designed for safety from the ground up.
Functional safety and open source are not incompatible. But the path to compatibility is architectural. It begins with drawing boundaries, enforcing separation, and using OSS where it makes sense, not where it creates risk.
There is a seductive simplicity to checklist-driven safety. It feels concrete. It promises a clear path to certification. But for something as complex and dynamic as Linux, that promise is misleading.
Safety is not paperwork. It is architecture. It is about making sure that your system behaves as expected, even when things go wrong. It is about designing with failure in mind.
EB corbos Linux for Safety Applications shows what that mindset looks like in practice. It does not fight Linux. It contains it. It controls it. And it proves that with the right architecture, open-source innovation and functional safety can coexist.
If your team is exploring how to bring Linux into a safety-critical system, start not with audits, but with architecture. That is where safety begins.
Ready to try EB corbos Linux for Safety Applications for free? Your download is available here.



